Your Information Is Safe With Us. The Data Center will never sell, rent, share or distribute your personal details with anyone. In addition, we will never spam you.
Last month a new ransomware strain appeared called “Cry” or “CryLocker,” which uses PNG, or Portable Network Graphic image files to record target users’ information such as the encrypted files themselves, as well as their location, and then uploads an image of this data to an album on image-sharing sites such as Imgur.com.
CryLocker was discovered by the security research activist MalwareHunter Team, and communicates using UDP (User Datagram Protocol). It also poses as a fake organization called the “Central Security Treatment Organization”. After it appends the file extension .cry to the victims’ files, it demands roughly 1.1 bitcoins, or $625 USD to get the private decryption key to unlock the files. Here’s a screenshot of CryLocker, also detected by the filename Ransom_MILICRY.A:
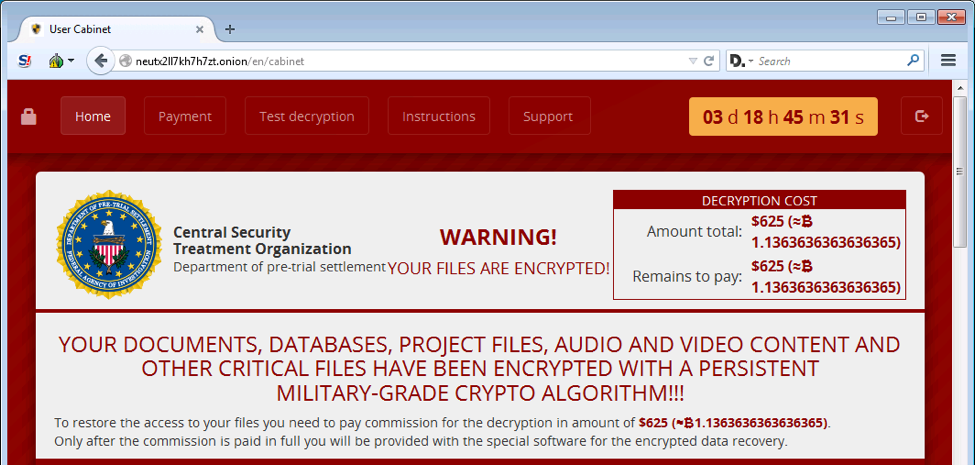
How CryLocker Encrypts Files
When CryLocker infects a computer it makes a backup of certain shortcuts on the victim’s Windows desktop and saves them in a folder on the desktop called old_shortcuts. The purpose of this folder is currently unknown.
The MalwareHunter Team found some anomalous characteristics of this new ransomware strain not seen in previous strains (although some basic traits resemble Cerber). In addition to the aforementioned use of UDP and posting images of the data stolen from target users’ databases, it also queries Google Maps API to find out the victims’ physical location using proximal wireless SSIDs.
CryLocker has been documented being distributed by way of the Sundown exploit kit. According to Trend Micro, it’s also being “dropped via the Rig exploit kit”. Trend Micro also reports that CryLocker also exhibits another anomaly: There is no related or previously-detected ransomware family connected to this new strain. Security researchers are saying that all these anomalies are employed in order to further hide cybercriminals’ location and identities.
Other cybersecurity specialists are theorizing that the Imgur image-posting tactics are also employed so that there will be a permanent record that ransomware peddlers can refer back to. A new PNG file is uploaded to Imgur every time a new database or PC is infected. This may also be in case the cyber crooks have to alter their C&C IP addresses. The data-heisters can also easily hide the real C&C server amongst the 4096 IP addresses they use to broadcast the unique PNG files, to further cover-up their identities and deeds.
According to BleepingComputer.com, “The use of UDP packets is probably being done to obfuscate the location of the Command & Control server so that authorities cannot seize it.” Here’s a screenshot of UDP packets being “trafficked” on the SmartSniff network monitoring utility:
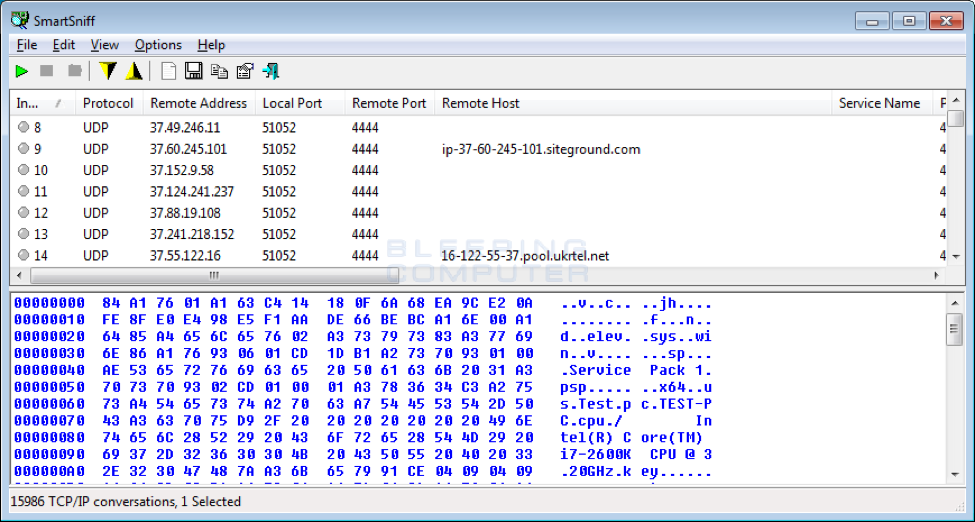
Files Associated with CryLocker Ransomware:
%UserProfile%AppDataLocalTemp[random_chars].exe
%UserProfile%AppDataLocalTemp[random_chars].tmp
%UserProfile%AppDataLocalTemp[random_chars].html
%UserProfile%Desktop!Recovery_[random_chars].html
%UserProfile%Desktop!Recovery_[random_chars].txt
%UserProfile%Desktopold_shortcuts
C:WindowsSystem32Tasks[random_chars]
C:Templol.txt
(Source: BleepingComputer.com)
Authorities including the FBI advise never paying ransomware demands, but instead getting free file decryption tools, or letting an IT professional guide you through the process of cleanly unlocking your files using decryption tools and processes that will restore your PC data in fast order.
Have Questions About Ransomware and Cybersecurity?
If you have questions regarding ransomware and cybersecurity, The Data Center is a proven leader in providing IT consulting in Albany. Contact one of our expert IT staff at (518) 459-DATA (3282) or send us an email at info@thedatacenterny.com today, and we can help you with any of your questions, concerns, or needs.